- Products & Services
Threat Intelligence
Threat Detection and Response
Security Gateway
Security Services
- Solutions
- Partners
- About Us
Core Capabilities
Integrated detection and interception for perimeter security
Dual-Engine High-Fidelity Threat Detection
High-Fidelity Threat Detection
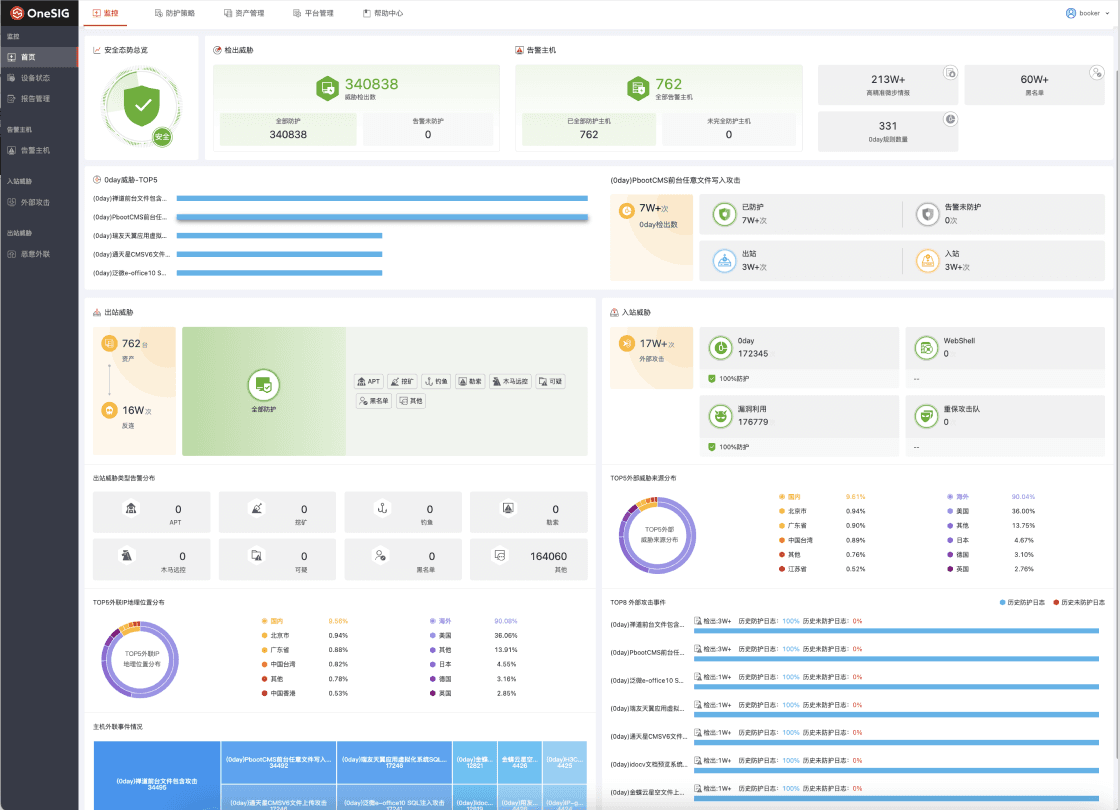

Dual-Engine High-Fidelity Threat Detection
- Dual detection engines powered by threat intelligence and intrusion prevention.
- Bidirectional traffic detection for accurate identification of various intrusion and variant attacks.
- False positive rate below 0.03%.
- Detect over 90% of intrusion attempts at the network perimeter.
Highly Effective Zero-day Exploit Prevention
Zero-day Exploit Prevention


Highly Effective Zero-day Exploit Prevention
- Convert industry-leading zero-day vulnerability intelligence into protection rules.
- Support detection of 350+ zero-day vulnerability signatures.
- Effectively protects against zero-day vulnerability attacks, with a protection rate of up to 81%.
Precise Detection of Compromised Threats
Compromised Threats Detection


Precise Detection of Compromised Threats
- Accurately locate compromised internal hosts based on millions of high-fidelity IOCs.
- Quickly blocks outbound connections from compromised hosts to prevent further damage.
Flexible and Granular Security Policy Customization
Security Policy Customization


Flexible and Granular Security Policy Customization
- Flexible customization of security policies based on business assets, threat types, severity levels, attack vectors, and custom fields.
- Enable more granular and adaptive protection aligned with specific business requirements.
Open and Compatible Integrated Blocking
Integrated Blocking


Open and Compatible Integrated Blocking
- Seamlessly integrate with third-party traffic detection devices or situational awareness platforms via API or Syslog.
- Facilitate massive blocking demands, seamlessly integrating into existing security operation systems, significantly enhancing the enterprise's defense capabilities.
High-Performance Interception and Blocking
High-Performance Interception


High-Performance Interception and Blocking
- High-performance underlying architecture capable of handling tens of gigabits of traffic and millions of blocking rules.
- Handle high-intensity security challenges with ease.
Product Advantages

Intelligence-driven
- Advanced threat intelligence, including high-risk vulnerabilities and high-fidelity IOCs, enables proactive and precise defense.

On-demand Blocking
- Effortlessly handle large-scale attacks. Seamlessly integrate with third-party devices for efficient threat mitigation. Customizable blacklists and whitelists ensure tailored protection for various business requirements.

Advanced Defense
- Dual-stack protocol support ensures seamless adaptation to next-generation networks. Flexible deployment options including inline and bypass modes. Unified detection and interception for maximum efficiency.

Intelligence-driven
- Advanced threat intelligence, including high-risk vulnerabilities and high-fidelity IOCs, enables proactive and precise defense.

On-demand Blocking
- Effortlessly handle large-scale attacks. Seamlessly integrate with third-party devices for efficient threat mitigation. Customizable blacklists and whitelists ensure tailored protection for various business requirements.

Advanced Defense
- Dual-stack protocol support ensures seamless adaptation to next-generation networks. Flexible deployment options including inline and bypass modes. Unified detection and interception for maximum efficiency.


Start your free trial now
Experience precise, efficient and intelligent threat detection and response